Unprotected Admin Functionality With Unpredictable URL – Lab Outline
This is a walk-through of a lab on the PortSwigger Web Security Academy site. It’s the second lab in the ‘Access Control’ section. The reading material can be found on this page and the lab can be found here.
In this lab, the admin panel is still unprotected. The objective remains the same as in the previous lab. Which is to first find the admin panel. Then delete the user ‘carlos’. The reading material prior to the lab on the Web Security Academy site hints at the solution. More on this as we continue. This lab does not require any additional tools to complete.
Steps Taken To Solve The Lab
I still searched the robots.txt file mentioned in the previous lab to see what would happen. This time, it resulted in a “Not Found” error.
The hint mentioned in the reading material was that the application can leak the URL to users in the JavaScript files. With this in mind, I opened the inspector—this can be done in firefox by right clicking and clicking inspect or by pressting ctrl+shift+c. Then I did a search for the word admin. I came across a script containing ‘adminPanelTag.setAttribute’. Inside of this was ‘/admin-tjf27c’, among other things.
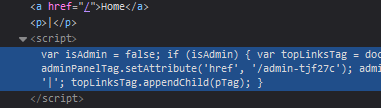
I added it to the URL and successfully landed at the unprotected admin panel. I deleted ‘carlos’ and completed the lab.
